1.0 Purpose
Information is an asset that is essential to fulfilling the mission of Lehigh University (the “University”) and needs to be suitably protected. This policy establishes the framework for the University’s Information Security Program. The Information Security Program is designed to protect institutional data from a wide range of threats, ensure operational continuity, minimize risk, and allow the University to focus on its mission.
The program is intended to:
- Provide a risk-based framework for the University to comply with legal, contractual, and regulatory requirements to protect information through policies, standards, processes, controls, and organizational structures.
- Secure University information systems from intentional or accidental damage and to protect information from threats to confidentiality, integrity or availability.
- Designate the appropriate roles and responsibilities to protect information and information systems.
- Provide specific guidance for individuals and groups of users to protect University data, systems, resources, and services.
2.0 Scope
This policy applies to everyone who accesses University data or information resources (including, but not limited to, all University staff, faculty, researchers, students, visitors, vendors, contractors, volunteers, and business partners) and all University information systems and resources.
3.0 Introduction
A number of standard information frameworks are available for the University to implement and each has its advantages. The University elects to deploy a hybrid framework for information security. This hybrid approach is designed to meet our University’s unique mission, business objectives, and compliance requirements. The framework draws upon the National Institute of Standards and Technology (NIST) Cyber Security Framework (CSF) and NIST 800-171 to ensure thoroughness and to comply with applicable current and future federal mandates, including around research and Title IV funding, while allowing for flexibility where less security is required.
In addition to guidance from NIST, Lehigh University recognizes areas where more specific security and privacy controls are required. These include:
- The Payment Card Industry Data Security Standard (PCI DSS) for University merchant accounts.
- The FBI’s Criminal Justice Information Services Division (CJIS) for University Police.
- Family Educational Rights and Privacy Act (FERPA).
- Gramm-Leach-Bliley Act (GLBA).
- Health Insurance Portability and Accountability Act (HIPAA).
- Export controls and International Traffic in Arms Regulations (ITAR) requirements.
- Institutional Review Board (IRB) and grant-specific stipulations for data protection.
- General Data Protection Regulation (GDPR), as applicable, and other privacy legislation and regulation, State Data Breach Laws, and applicable regulatory requirements.
Certain capitalized terms used in this policy are defined in Section 9.
4.0 Policy
All University data must be protected according to the provisions below:
- Risk Management: Data protections should be appropriate to the calculated impact to confidentiality, integrity, and availability of data or data systems.
- Risk Acceptance: Senior Management has the authority to accept information security, privacy, and compliance risks for the University.
- Data Classification: All university data is classified into levels based on its sensitivity and risk of harm if the data were to be lost, changed, or disclosed.
- Data Security: The university maintains minimum security controls appropriate to data classification levels.
- Privacy Review: Access to sensitive data required to operate information security program is provided only as required and is monitored and periodically reviewed.
- Compliance: University data must be protected in accordance with laws and regulations applicable to the University’s operations and other requirements imposed by contract.
5.0 Information Security Policy Framework:
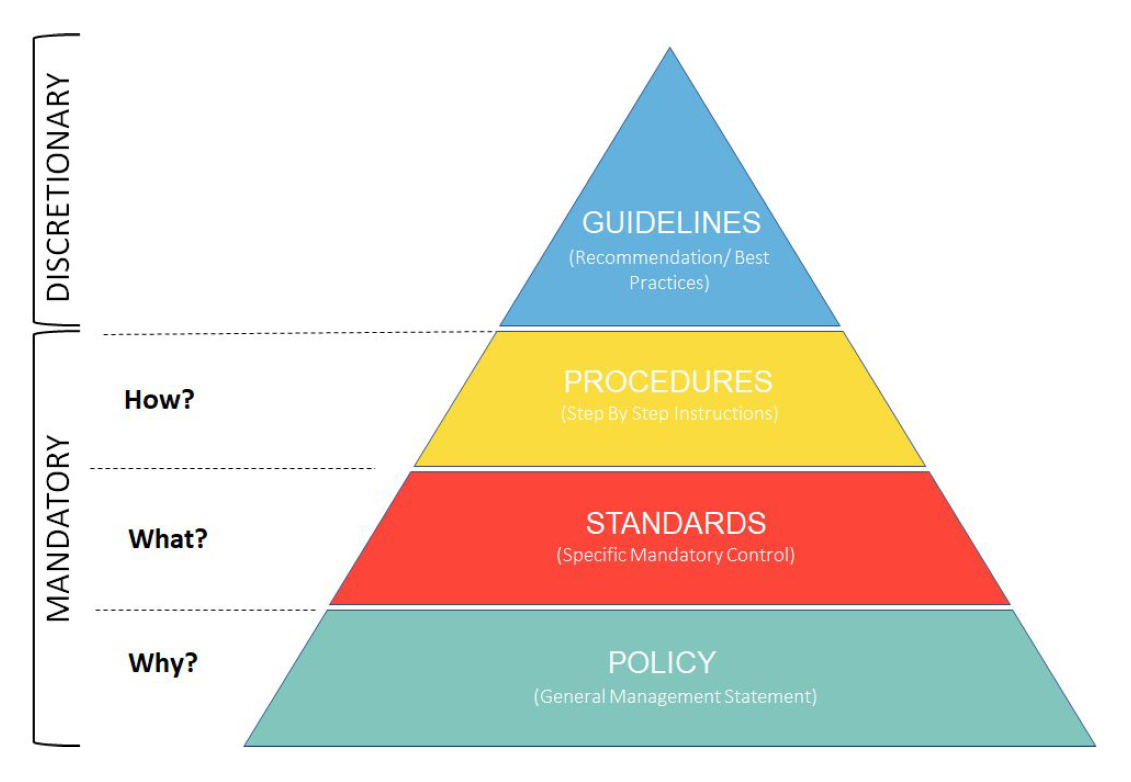
The objective of information security policies, procedures, and guidelines is to provide senior management with direction and support for decisions related to information security in accordance with Lehigh’s mission, business requirements, and governing laws and regulations. Information security policies will be approved by senior management or reviewed by appropriate policy committees (i.e. CGRC, ACIS), and published and communicated to all affected members of the University community and relevant external parties. These policies will establish the University’s approach to managing information security and will align with relevant federal, state, and regulatory information protection policies. Procedures (Processes), standards, and guidelines will be more specific. They will be created by departments or individuals and provide operational guidance for specific actions to be taken and minimum baseline security requirements to be met or other activities.
The Information security program will be reviewed at planned intervals (i.e. annually) or if significant changes occur to ensure its continuing efficacy. Each policy/standard/procedure will have an owner who has the responsibility to ensure it functions appropriately within our security framework in response to changes to the environment, new threats and risks, business circumstances, legal and policy implications, and technical environment.
Information security policies have the broadest scope because they form the foundation of the information security program. Therefore, policies will be approved through our ACIS Governance group. Policies that may have broader organizational impact may be referred to General Counsel or the University Trustees.
Standards, procedures, and guidelines will be developed and maintained by individuals who are responsible for specific operational procedures.
I. Policy
Established by Senior Management to reflect the University's values, principles, and strategies. The provide broad guidance to more specific standards and procedures.
II. Standards
Specify measurable requirements for compliance with university policies and applicable regulations and laws.
III. Procedures
Detailed plans to accomplish specific tasks or deliver services to meet the needs of the community while satisfying the requirements of applicable standards and policies. Developed and maintained by expert practitioners.
IV. Guidelines/Best Practices
Provides best practices relative to a particular topic or audience. For example, a summary of security tips for research faculty or for undergraduate students.
6. Review
The information security program needs to be continuously monitored, reviewed, and improved to ensure that it reflects the dynamic security requirements of the University and maintains the University’s exposure to risk at a level acceptable to senior management in relation to the University’s operational and business needs.
The Chief Information Security Officer (CISO) is responsible for ensuring this policy is annually reviewed.
7. Compliance and Enforcement
Violations of this policy and/or any standard or procedure published under this policy may result in suspension or loss of user privileges, for the purpose of protecting the University’s information and/or information systems. Additional administrative sanctions may apply up to and including termination of employment or contractor status with the University. Civil, criminal, and equitable remedies may also apply.
8. Security & Privacy Control Families
Policies, standards, procedures, and guidelines will be developed in the context of the following control families for the purpose of providing appropriate security controls and to allow the University to validate compliance with legal and regulatory requirements.
Access Control [800-171]
Limit information system access to authorized users, processes acting on behalf of authorized users, or devices (including other information systems), and to the types of transactions and functions that authorized users are permitted to exercise.
Assessment, Authorization, and Monitoring [800-53 Rev 5]
The Chief Information Security Officer is responsible to ensure development, documentation, and dissemination of policies, procedures, standards, and guidelines designed to protect the privacy and security of information and information systems, assess the effectiveness of the controls, monitor for deviations, and ensure senior management authorizes systems and accepts inherent risk.
Audit and Accountability [800-171]
Create, protect, and retain information system audit records to the extent needed to enable the monitoring, analysis, investigation, and reporting of unlawful, unauthorized, or inappropriate information system activity; and ensure that the actions of individual information system users can be uniquely traced to those users so they can be held accountable for their actions, all in accordance with the University’s applicable policies, rules, and regulations existing from time to time, including the University’s Acceptable Use of Computer Systems and Facilities Policy, as amended.
Awareness and Training [800-171]
Ensure that managers and users of information systems are made aware of the security risks associated with their activities and of the applicable policies, standards, or procedures related to the security of information systems; and ensure that personnel are adequately trained to carry out their assigned information security-related duties and responsibilities.
Configuration Management [800-171]
Establish and maintain baseline configurations and inventories of information systems (including hardware, software, firmware, and documentation) throughout the respective system development life cycles; and establish and enforce security configuration settings for information technology products employed in information systems.
Contingency Planning [800-53]
Create an acceptable plan for recovering information systems and data following an emergency or system disruption. Ensure the plan is tested periodically and deviations are reported to authorized officials.
Identification and Authentication [800-171]
Identify information system users, processes acting on behalf of users, or devices and authenticate (verify) the identities of those users, processes, or devices, as a prerequisite to allowing access to information systems.
Incident Response [800-171]
Establish and maintain an operational incident-handling capability for information systems that includes adequate preparation, detection, analysis, containment, recovery, and user response activities; and track, document, and report incidents to appropriate officials and/or authorities.
Individual Participation [800-53 Rev 5]
Establish policies, standards, and procedures to ensure individuals are aware of Lehigh’s privacy policies, provide consent to use their data, and are aware of their rights for redress in accordance with our policies and applicable laws and regulations.
Maintenance [800-171]
Perform periodic and timely maintenance on information systems; and provide effective controls on the tools, techniques, mechanisms, and personnel used to conduct system maintenance.
Media Protection [800-171]
Protect information system media containing sensitive information, both paper and digital; limit access to sensitive information on information system media to authorized users; and sanitize or destroy information system media containing sensitive information before disposal or release for reuse.
Personnel Security [800-171]
Screen individuals prior to authorizing access to information systems containing sensitive information and ensure that sensitive information and information systems containing sensitive information are protected during and after personnel actions such as terminations and transfers.
Physical and Environmental Protection [800-171]
Limit physical access to information systems, equipment, and the respective operating environments to authorized individuals; and protect the physical plant and support infrastructure for those information systems.
Privacy Authorization [800-53 Rev 5]
Establish policies and procedures to ensure that Lehigh has the authority and a specific purpose to collect personally identifiable information and that such information is shared with external parties only as needed and with the appropriate security controls in place.
Program Management [800-53]
The Chief Information Security Officer (CISO), under the direction of the Vice Provost for Library and Technology Services, is required to develop and maintain an institution-wide information security program. The CISO must periodically report on the status of the program to senior management and/or Board of Trustees on the goals of the program, status relative to goals, prevalent risks, and resources required to support the program.
Risk Assessment [800-171]
Periodically assess the risk to operations (including mission, functions, image, or reputation), assets, and individuals, resulting from the operation of information systems and the associated processing, storage, or transmission of sensitive information.
Security Assessment [800-171]
Periodically assess the security controls in information systems to determine if the controls are effective in their application; develop and implement plans of action designed to correct deficiencies and reduce or eliminate vulnerabilities in information systems; and monitor information system security controls on an ongoing basis to ensure the continued effectiveness of the controls.
System and Communication Protection [800-171]
Monitor, control, and protect communications (i.e., information transmitted or received by information systems) at the external boundaries and key internal boundaries of the information systems; and employ architectural designs, software development techniques, and systems engineering principles that promote effective information security within information systems.
System and Information Integrity [800-171]
Identify, report, and correct information and information system flaws in a timely manner; provide protection from malicious code at appropriate locations within information systems; and monitor information system security alerts and advisories and take appropriate actions in response.
System and Services Acquisition [800-53]
Security and privacy functional requirements must be included when systems and services are acquired or developed which may involve sensitive data. Complementary controls might be needed and funding should be bound to the purchase and ongoing maintenance of the system and service.
9. Definitions
- ACIS - The Advisory Council for Information Services (ACIS) is an appointed body which is representative of the major academic and administrative division of the university. ACIS was created to advise the provost on campus policies relating to Library and Technology Services' (LTS) responsibilities. ACIS reviews and approves policies developed by LTS staff. These policies are also circulated to the campus community for comment for a period of thirty days before they receive final ACIS approval and are then forwarded to the provost for adoption.
- Chief Information Security Officer - The individual responsible for understanding Lehigh University's mission and institutional interests and designing, implementing, and maintaining an information security program to protect them.
- Control - A protective measure against threats. Three types: management, operational or technical.
- Management controls: The security controls that focus on the management of risk and the management of information system security.
- Operational controls: The security controls that are primarily implemented and executed by people (as opposed to systems).
- Technical controls: The security controls that are primarily implemented and executed by the system through the system's hardware, software, or firmware.
- Data - Information in any form (i.e. electronic or in a physical format).
Data Classification - Classifying University data based on levels of sensitivity and value is an integral part of our data security framework at Lehigh University. It provides the foundation to allow us to protect sensitive data while simultaneously providing broad, open access to data in all of its forms. Our classification policy defines 4 classes of data from critical (Class I) to public (Class IV). Decisions about data types not explicitly defined in this policy should be made by the Data
Stewards overseeing the data. See https://oirsa.lehigh.edu/classification-data
- Data Governance and Standards Committee - The mission of the DGSC is to promote appropriate data use through planning, policy, and protocols at Lehigh. Responsibilities include overseeing the data classification scheme.
- Data Stewards - A Data Steward is a senior-level employee of the University who oversees one or more sets of Institutional Data and have planning and policy-level responsibilities for data in their functional areas.
- FERPA - The Family Educational Rights and Privacy Act (FERPA) (20 U.S.C. § 1232g; 34 CFR Part 99) is a Federal law that protects the privacy of student education records. The law applies to all schools that receive funds under an applicable program of the U.S. Department of Education.
- GDPR - General Data Protection Regulation is a regulation in EU law that governs data protection and privacy within the European Union.
- GLBA - Gramm-Leach-Bliley Act. is a banking law which applies to higher education institutions because of our role with student loans.
- Guidelines - Recommended actions and operational guides to users, IT staff, operations staff, and others when a specific standard does not apply. Guidelines may be technology specific. Guidelines are created by cross-organizational working groups consisting of subject matter experts.
- HIPAA - The Health Insurance Portability and Accountability Act of 1996 is a law that provides data privacy and security provisions for safeguarding medical information.
- Information System - A resource used for electronic storage, processing, or transmitting of any data or information, as well as the data or information itself. This definition includes but is not limited to electronic mail, voice mail, local databases, externally accessed databases, CD-ROM, recorded magnetic media, photographs, digitized information, or microfilm. This also includes any wire, radio, electromagnetic, photo-optical, photo electronic, or other facility used in transmitting electronic communications, and any computer facilities or related electronic equipment that electronically stores such communications.
- ITAR - International Traffic in Arms Regulations (ITAR) are regulatory controls governing the export and import of defense-related articles and services on the United States.
- NIST - National Institute of Standards and Technology is a part of the Department of Commerce that publishes federal standards to assess cybersecurity programs.
- 800-171 contains a list of requirements that any non-Federal computer system must follow in order to store, process, or transmit Controlled Unclassified Information (CUI) or provide security protection for such systems.
- 800-53 Rev. 5, Security and Privacy Controls for Information Systems and Organizations is a more comprehensive list of requirements previously required for Federal systems and data but now broadly applied.
- Policy - An overall general statement of principle that provides scope and direction. IT policies are broad and are approved through the University’s ACIS committee.
- Procedures - Detailed step-by-step tasks that should be performed to achieve a certain goal and are often dependent on the technology being implemented. Procedures are often created by local or departmental groups and are shared when needed.
- Senior Management - University Leadership with the authority to accept risk for the University.
- Sensitive Information - Information that is designated as Class I or Class II Information under the Data Classification Standards.
- Standard - Refers to mandatory activities, actions, rules, or regulations and are not dependent on a specific technology. Standards are created by cross-organizational working groups consisting of subject matter experts.
- Vice Provost of Library and Technology Services - Individual responsible for understanding Lehigh University’s mission and institutional interests and designing and implementing information systems to enable the achievement of these goals.
10.0 Reference Documents:
11.0 Additional Contacts:
| Subject | Contact | Phone | |
|---|---|---|---|
| Information Security | security@lehigh.edu |
Responsible University Official: Eric Zematis, CISO
Responsible University Office: Lehigh Library and Technology Services (LTS), 610-758-3994
Effective Date: 02/23/2020
Reviewed Date: 08/25/2021
Revision Number: 1